Azure AD Scim User Provisioning
Prerequisites
Integrate SCIM With LambdaTest:
- You will need an Enterprise plan with LambdaTest.
- SSO must be already integrated. Please complete LambdaTest SSO & Azure AD Integration
Integrating SCIM with Azure AD
Step 1: Sign in to your LambdaTest account. Don't have an account, register for free.
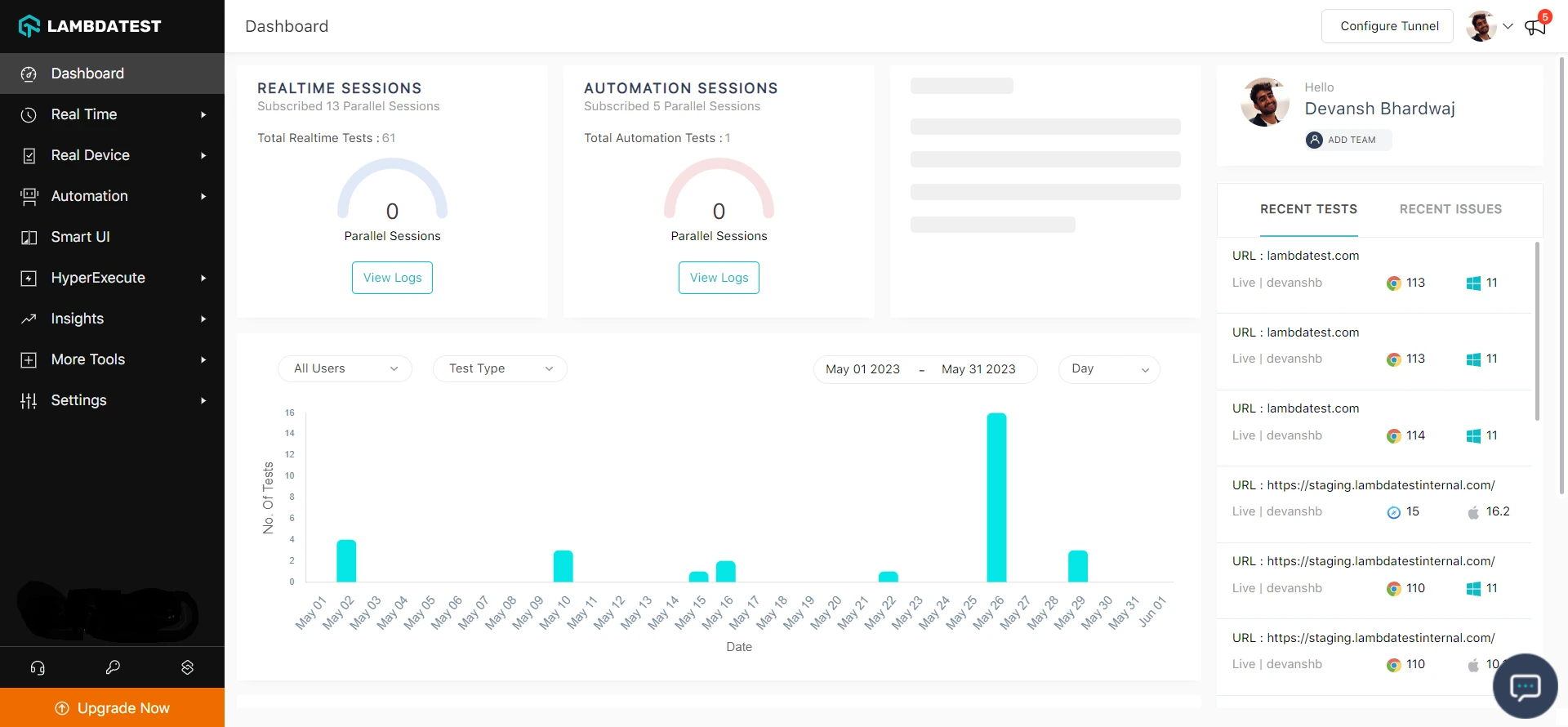
Step 2: Head to Settings and select Organization Settings from the dropdown.
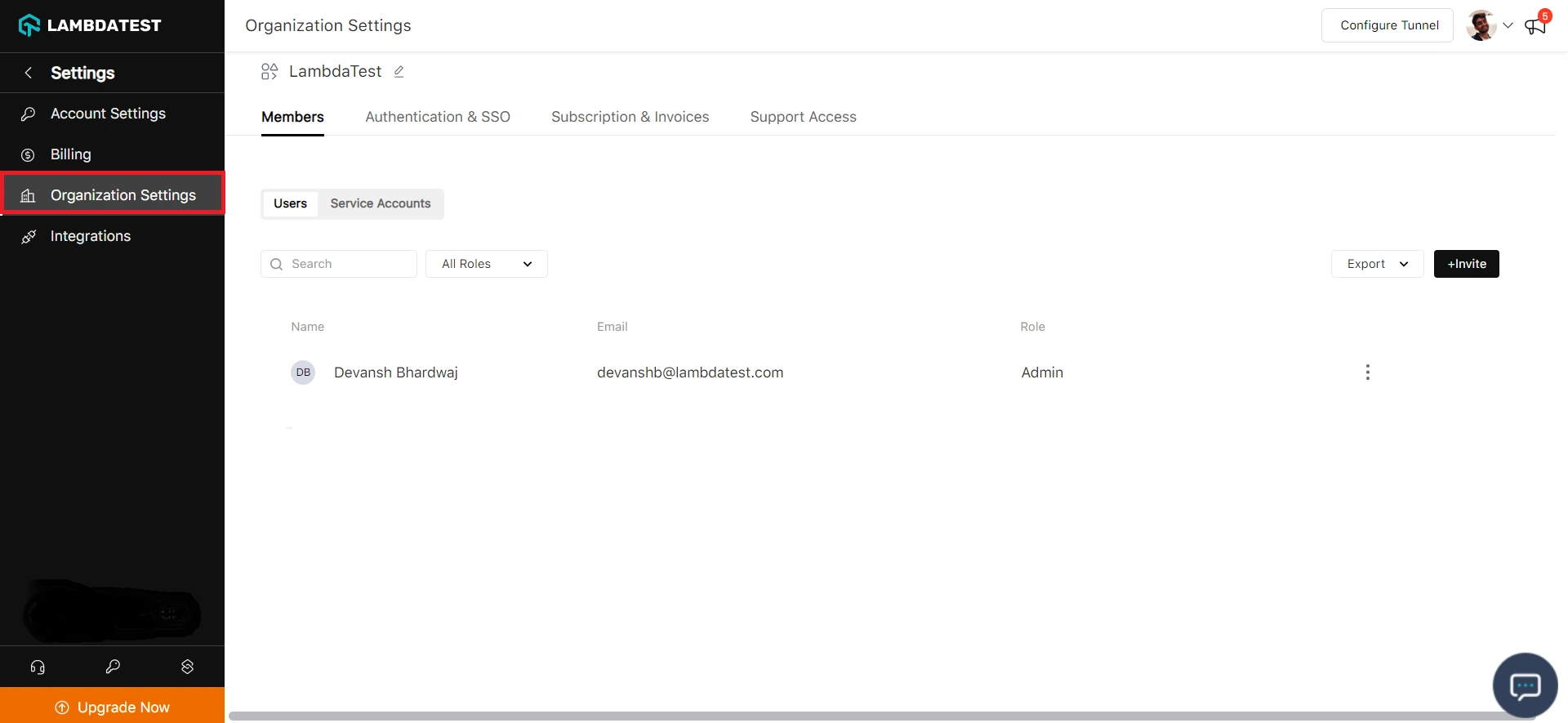
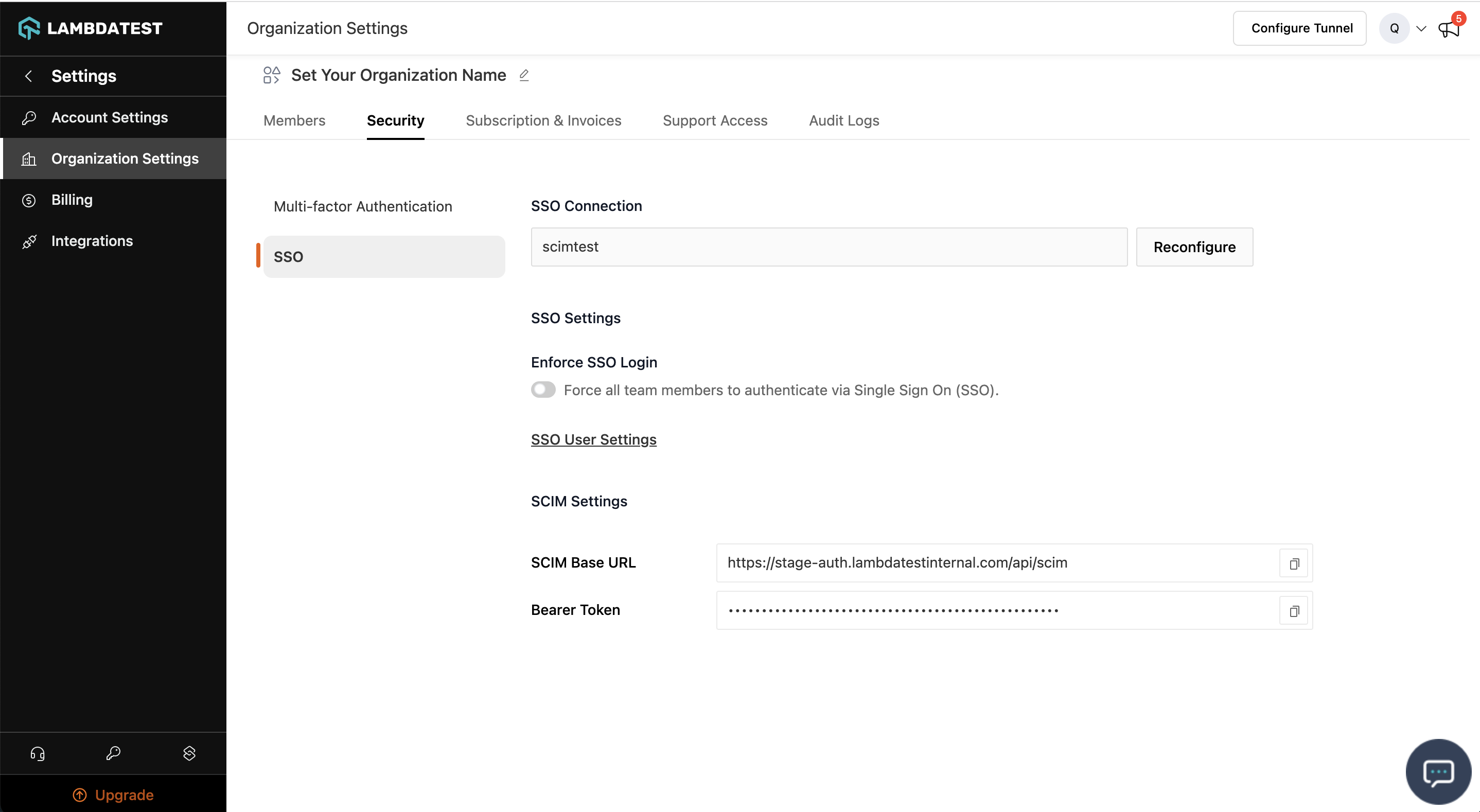
Step 3: Head to the Authentication and SSO tab and click and copy the SCIM Base URL and Bearer Token option.
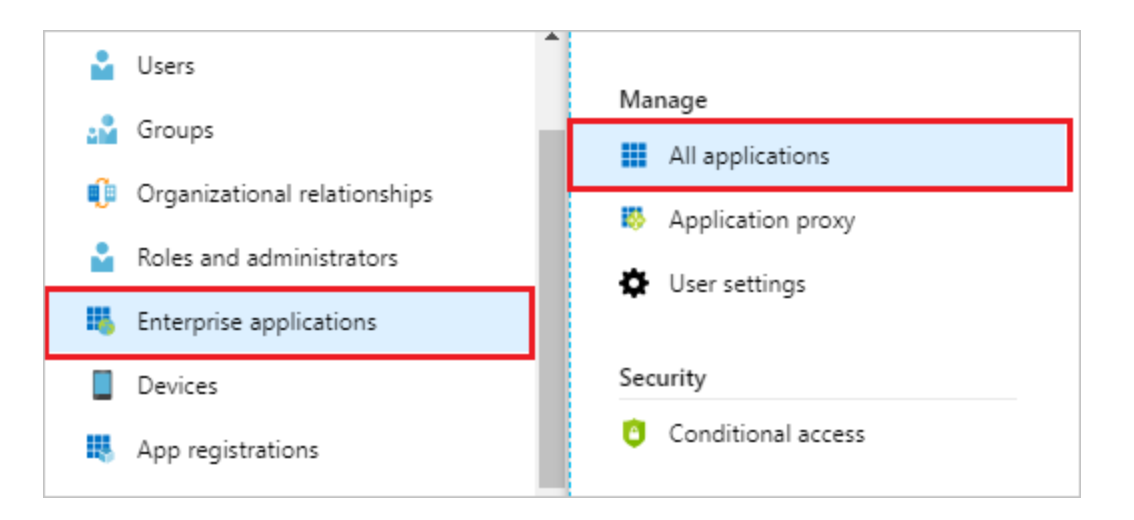
Step 4: Sign in to the Azure portal. Select Enterprise Applications, then select All applications.
Step 5: In the applications list, select application used for LambdaTest SSO setup
Step 6: Select the Provisioning tab.
Step 7: Under the Admin Credentials section, input your LambdaTest SCIM Base URL https://auth.lambdatest.com/api/scim?aadOptscim062020 and Bearer Token retrieved earlier in Step 3. Click Test Connection to ensure Azure AD can connect to LambdaTest. If the connection fails, ensure your LambdaTest account has Admin permissions and try again.

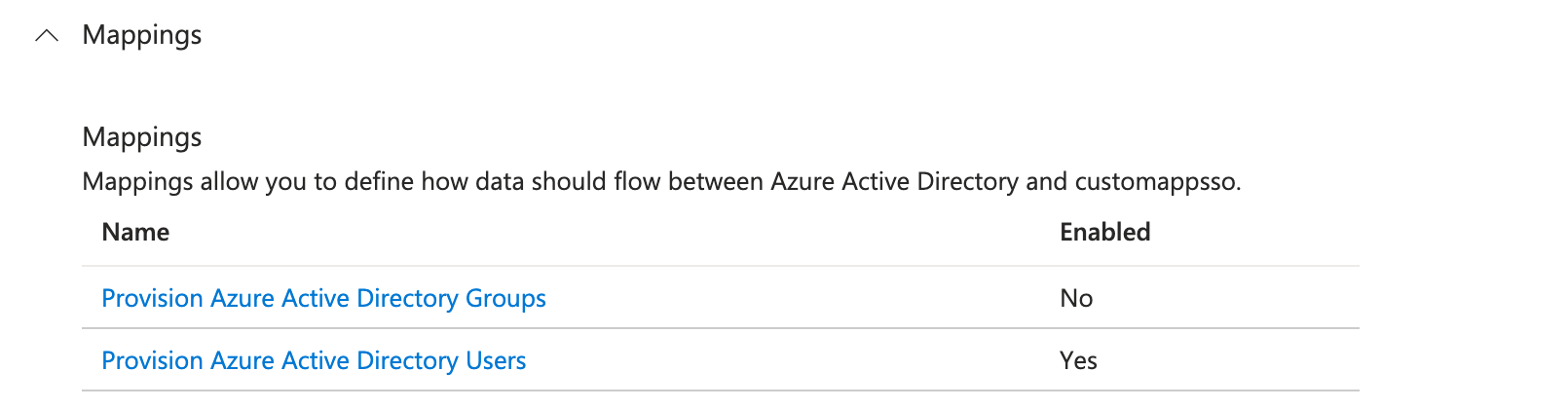
Step 8: Under the Mappings section, select Synchronize Azure Active Directory Users.
Step 9: Creating Custom Attributes
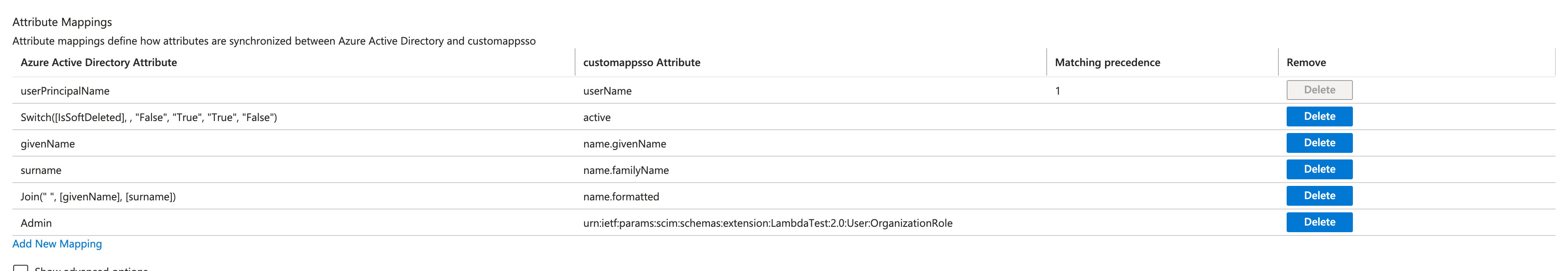
- Show advanced options > Edit attribute list for customappsso > Add attributes
- userName, Active, name.givenName, name.familyName are required attributes
-
urn:ietf:params:scim:schemas:extension:LambdaTest:2.0:User:OrganizationRole: Custom attribute used to set LambdaTest Organization Role for Users, If this attribute is not mapped User role would be set by default. Allowed values are (Admin/Guest/User) -
urn:ietf:params:scim:schemas:extension:LambdaTest:2.0:User:LambdatestGroup: Used to assign an existing group in Lambdatest to a new user created in lambdatest through SCIM. (Applicable only if organisation has group support active)
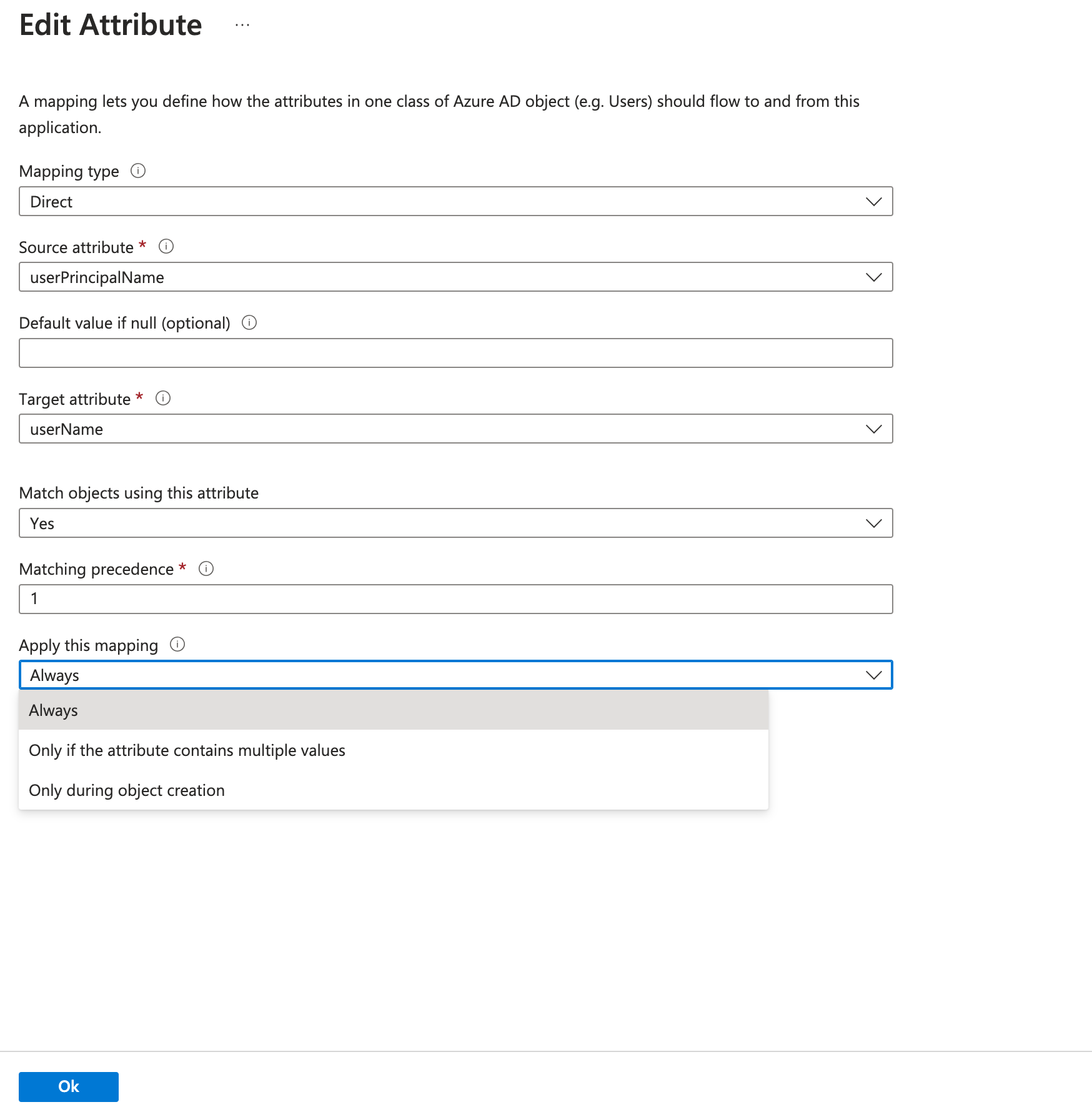
For filtering only userName attribute is supported and must be selected for filtering, click edit on userPrincipalName and make sure Apply this mapping is set to Always
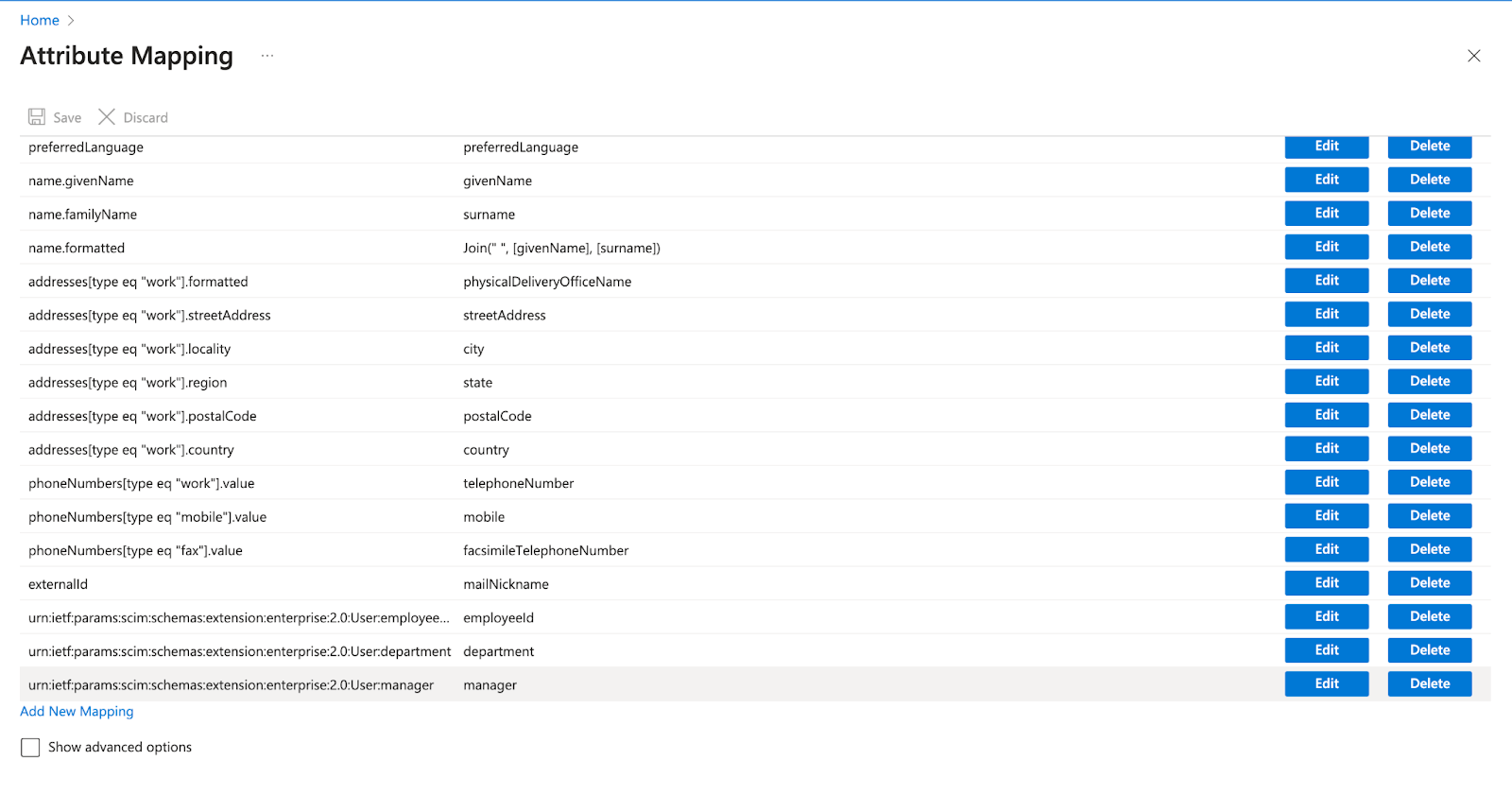
- Dynamic/Static assignment of custom attributes: After custom attribute creation, we have to map them using “Add new mapping”
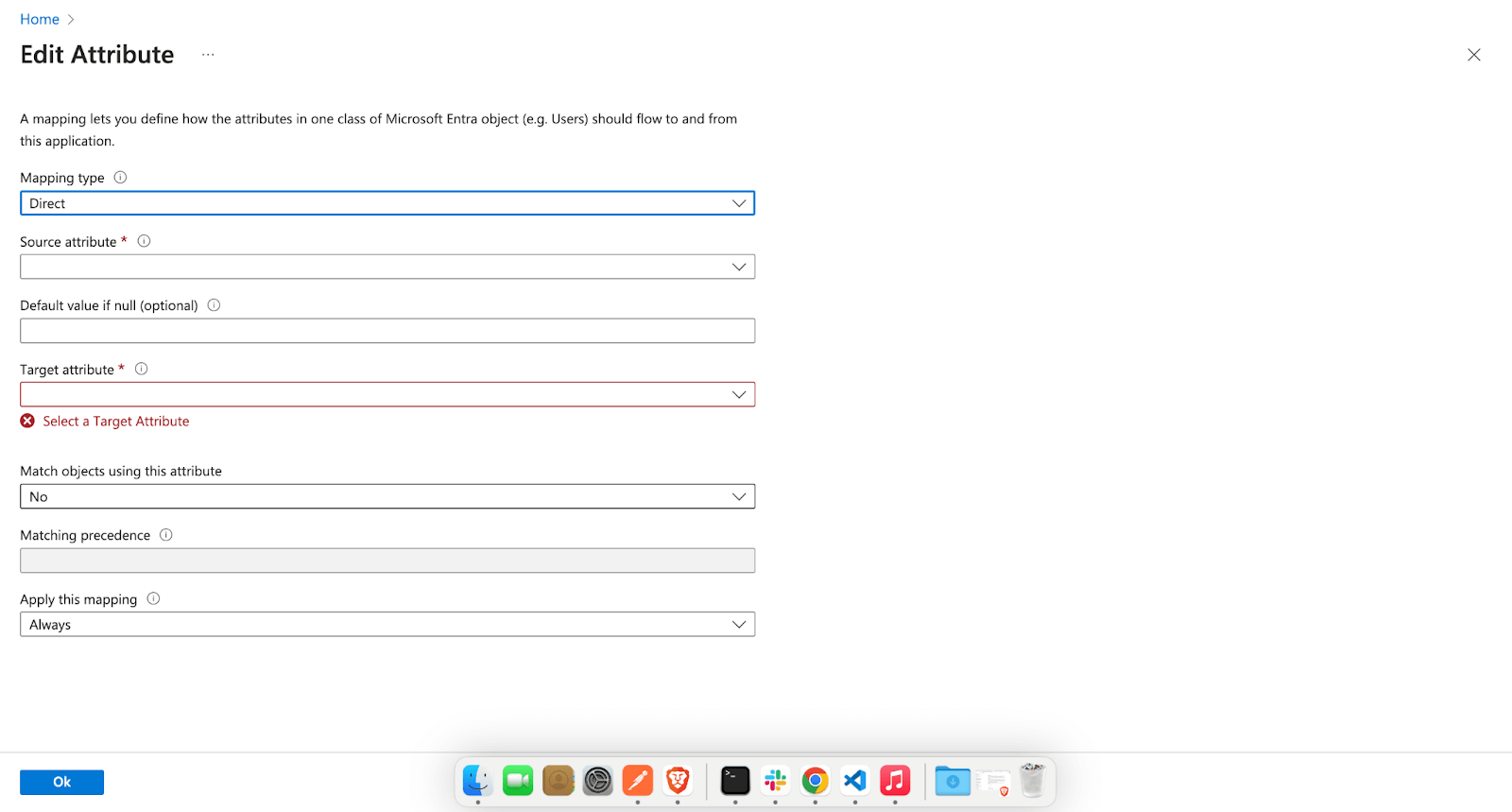
Now there are three types Mapping type in AzureAD, “Direct”, “Constant” and “Expression”.
For example we can set Constant association “Guest” for urn:ietf:params:scim:schemas:extension:LambdaTest:2.0:User:OrganizationRole
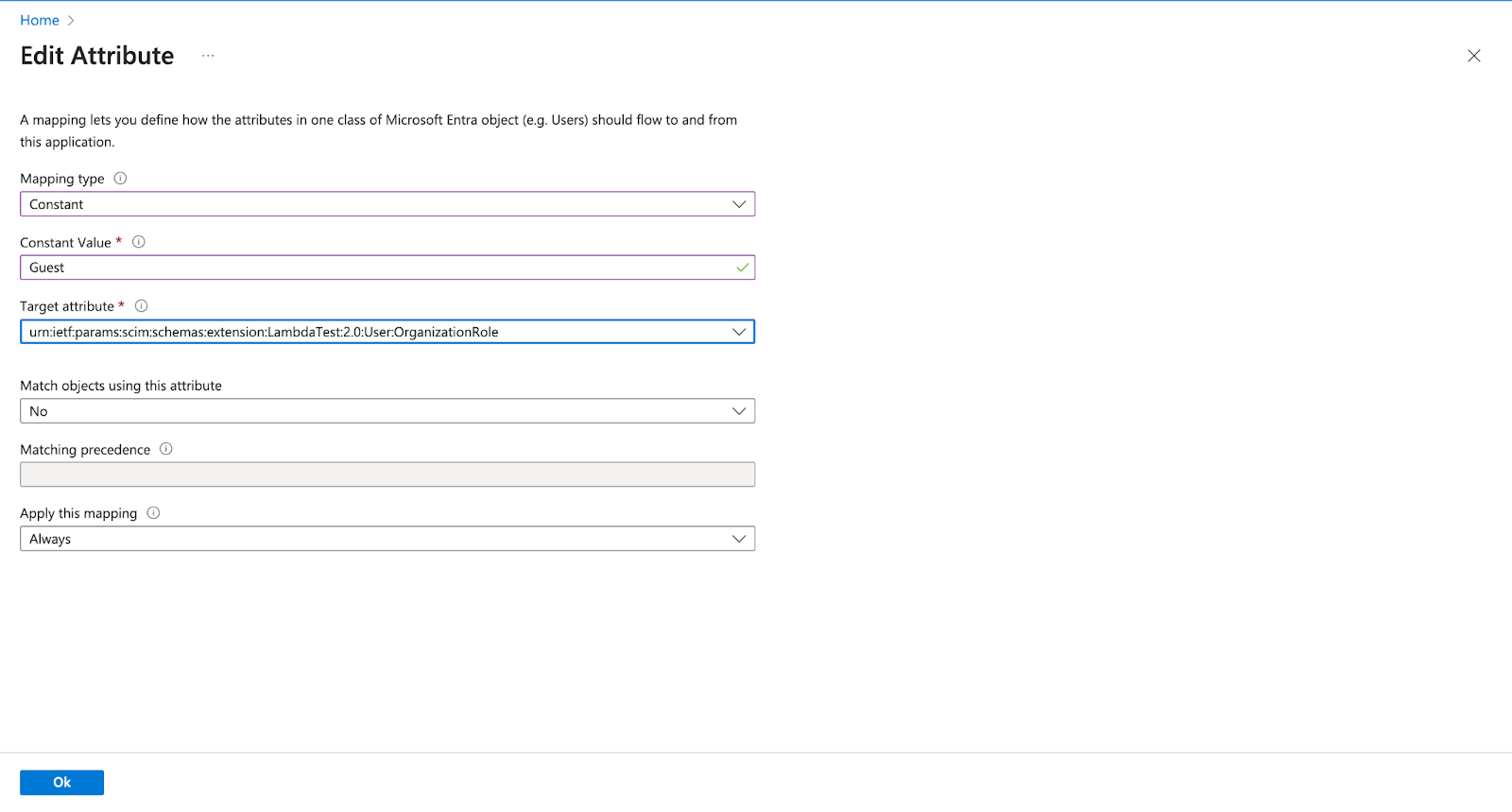
Or, can create association using the Expression like this ,
IIF(SingleAppRoleAssignment([appRoleAssignments])="Admin", "Admin",
IIF(SingleAppRoleAssignment([appRoleAssignments])="Guest", "Guest",
IIF(SingleAppRoleAssignment([appRoleAssignments])="User", "User", "User")))
In the above example we are using the appRoleAssignments attribute of microsoft user to set string value.
After custom attribute creation, we have to map them using “Add new mapping”
Step 10: To enable the Azure AD provisioning service for LambdaTest, change the Provisioning Status to On in the Settings section.
Step 11: When you are ready to provision, click Save.
This operation starts the initial synchronization cycle of all users in Scope in the Settings section. The initial cycle takes longer to perform than subsequent cycles, which occur approximately every 40 minutes as long as the Azure AD provisioning service is running.

That's all you need to know about LambdaTest SCIM Auto User Provisioning with Azure AD.In case you have any questions please feel free to reach out to us via the 24/7 chat support or email us over support@lambdatest.com.
