What Is a Proxy Server and How Does It Work
Zikra Mohammadi
Posted On: December 30, 2024
![]() 29424 Views
29424 Views
![]() 16 Min Read
16 Min Read
Proxy servers manage the flow of data between users and the Internet, acting as intermediaries to enable secure, efficient, and controlled communication with online resources. They enhance privacy, analyze traffic patterns, and offer various functionalities for individuals and businesses.
For web developers, proxy servers simplify debugging, performance optimization, and testing in different environments. They help emulate user scenarios, manage server loads, and ensure applications remain robust under various conditions.
TABLE OF CONTENTS
What Is a Proxy Server?
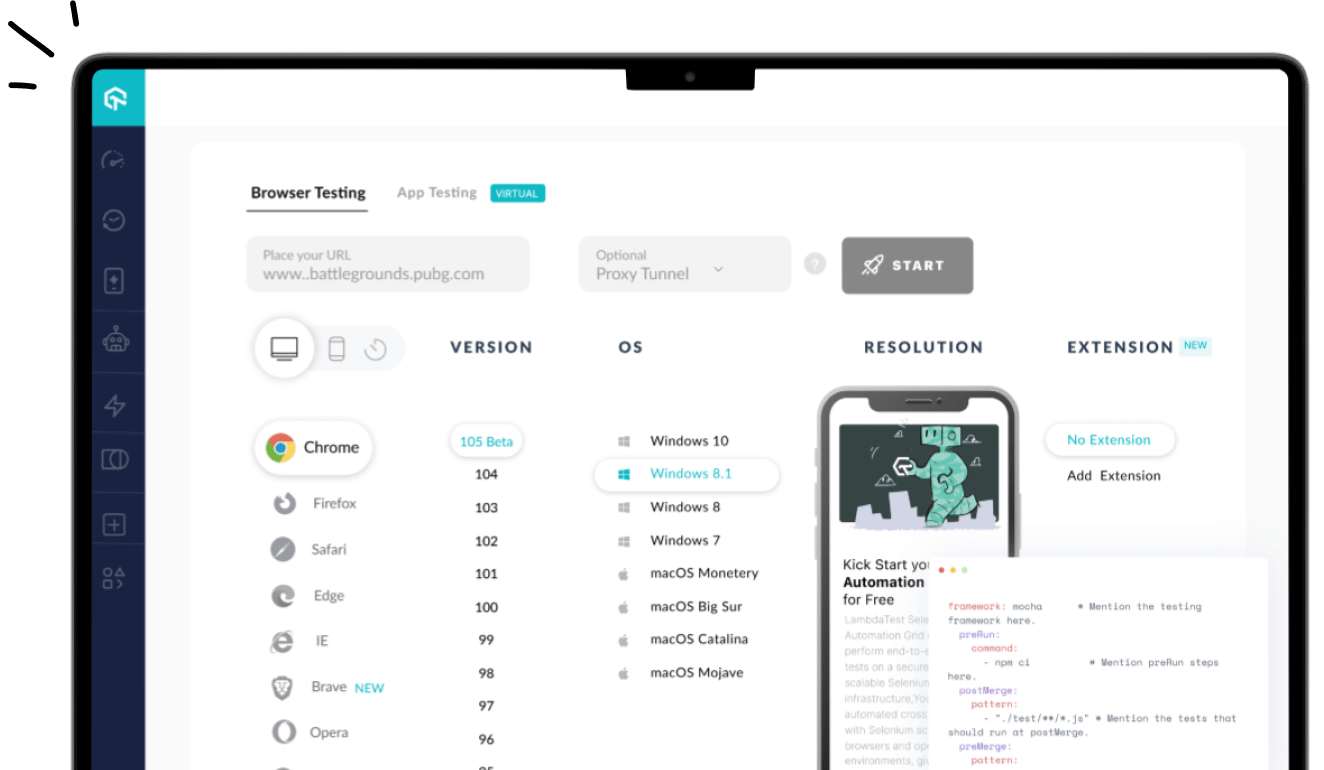
A proxy server is an intermediary system between a user’s device and the Internet, forwarding requests and responses. It acts as a gateway by processing requests from client devices, forwarding them to the target server, and relaying the server’s responses back to the user.
This server provides a layer of abstraction and control, enabling functionalities such as enhanced security, improved privacy, traffic management, and performance optimization. It also hides the client’s native IP address by using its own, helping to conceal the user’s identity and location from the websites they access.
Proxies are widely used for personal browsing, corporate networks, and web development tasks such as debugging, testing, and web scraping. Depending on the type, they can provide anonymity, filter content, or balance traffic loads for high-demand systems.
Understanding the features of proxy servers can help you choose the right one for your requirements.
- Forward Proxy: Intermediary for internal network clients, managing requests and enhancing IP security. Ideal for centralized control but may lack personalized configurations.
- Transparent Proxy: Routes traffic without user awareness. Useful for invisible proxies but vulnerable to security threats.
- Anonymous Proxy: Hides user identity for privacy. It may attract suspicion or platform limitations.
- High-anonymity Proxy: This proxy erases user data before connection. It is suitable for sensitive activities, but free options may be risky.
- Distorting Proxy: Masks real locations by altering IP addresses. Effective for location masking but may face website blocks.
- Data Center Proxy: Fast and cost-effective for data gathering and web scraping but offers less anonymity.
- Residential Proxy: This type of proxy uses IPs from physical devices. It is trusted for ad verification and fraud prevention. It is reliable but expensive.
- Public Proxy: Free and accessible, suitable for low-cost use but slow and insecure.
- Shared Proxy: Shared by multiple users, low-cost but risks bans if misused.
- SSL Proxy: Encrypts and decrypts data for security, valuable for preventing SSL threats but slower without caching.
- Rotating Proxy: Assigns unique IPs for continuous web scraping. Requires secure providers to avoid data exposure.
- Reverse Proxy: Positioned before servers, manages requests, and improves load balancing. Requires added security for server protection.
 Note
NoteRun your test directly on LambdaTest, even if your system is behind a proxy or protected by a firewall. Try LambdaTest Today!
Why Use a Proxy Server?
Proxy servers are crucial in web development. They enhance the process, ensure security, and improve performance.
Here’s a breakdown of their essential reasons:
- Enhancing Security: Security is a critical aspect of web development, and proxies offer multiple layers of protection.
- IP Masking: Proxies hide the real IP, protecting developers and users from malicious threats.
- Content Filtering: Proxies block harmful content before it reaches the network.
- Data Encryption: SSL proxies encrypt communication, preventing sensitive data interception.
- DDoS Mitigation: Proxies can filter out DDoS attacks, ensuring server stability.
- Managing and Analyzing Traffic: Proxies are invaluable for traffic monitoring and control in web development.
- Traffic Filtering: Block malicious traffic and prevent access to restricted content.
- Analytics: Proxies collect logs to help developers understand user behavior and optimize application design.
- Rate Limiting: Control server requests to prevent abuse or spikes in traffic.
- Facilitating Development and Testing: Proxies assist developers in testing web applications under varied conditions.
- Cross-Regional Testing: Emulate requests from different regions to test location-specific features and optimize user experience.
- Device-Specific Testing: Simulate requests from various devices and browsers.
- Debugging: Intercept and inspect HTTP/HTTPS requests and responses to help debug issues like incorrect API responses.
- Simulating Different Network Conditions: Proxies help developers simulate different network speeds and latencies to optimize applications.
- Simulating Low Bandwidth: See how applications perform on low-bandwidth networks to optimize resources like images and videos.
- Simulating High Latency: Test application responsiveness in high-latency environments, ensuring fault tolerance and stability.
- Optimizing Performance: Proxies can speed up web applications by optimizing data flow and reducing server load.
- Caching: Cache frequently accessed resources to reduce latency and improve response times.
- Load Balancing: Distribute incoming requests across multiple servers to ensure high availability.
- Compression: Compress data to conserve bandwidth and speed up delivery.
- Accessing Geo-Restricted Content: Proxies allow developers to access geo-restricted content, which is essential for development and testing.
- Bypassing Geofencing: Test how applications behave with content restricted to specific countries or regions.
- Localized Content Testing: Simulate access from different locations to test how content is localized for various regions.
- Handling API Testing: Proxy servers are efficient tools for API testing, enabling request monitoring and communication inspection.
- Request Monitoring: Inspect API requests and responses to identify issues like incorrect headers or slow responses.
- API Load Testing: Simulate real-world traffic to ensure APIs can handle high traffic volumes.
- API Response Manipulation: Intercept and modify API responses to test application behavior under different conditions.
- Testing Content Delivery Networks (CDNs): Proxies help developers evaluate the effectiveness of CDNs for fast content delivery.
- Performance Testing: Test content load speeds by routing requests through proxies from different regions.
- Load Time Evaluation: Identify potential bottlenecks in content delivery by simulating traffic from various locations.
- Server Reliability Testing: Test CDN servers’ ability to handle traffic spikes and maintain reliability during high-demand periods.
- Web Scraping for Competitive Insights: Proxy servers make ethical web scraping easier by hiding the IP address to avoid detection.
- Avoiding Detection: Rotate IP addresses to prevent servers from detecting or blocking scraping attempts.
- Competitive Intelligence: Scrape competitor data, market trends, and user feedback to drive better development decisions.
- Rotating Proxies: Use rotating proxies to ensure each request comes from a different IP, preventing detection by target websites.
The above points highlight why proxy servers are widely used and can be very beneficial. They make tasks easier and more efficient.
Proxy Server vs VPN
A proxy server masks the user’s IP address for specific applications but does not encrypt traffic, making it faster but less secure. When compared to a VPN, it encrypts all Internet traffic, offering robust security and privacy by protecting data and masking the user’s IP address across all applications.
Let us see the differences between a proxy and a VPN in detail:
| Aspects | Proxy Server | VPN |
|---|---|---|
| Functionality | Acts as an intermediary, masking the user's IP for specific applications. | Encrypts all Internet traffic, ensuring overall anonymity. |
| Encryption | No encryption, leaving data vulnerable to interception. | Provides robust encryption, protecting data from interception. |
| Scope of Coverage | Works on a per-application basis; only configured apps use the proxy. | Encrypts and secures all Internet traffic from the device. |
| Performance Impact | Faster as there’s no encryption overhead, but less secure. | It may reduce speed slightly due to encryption, but higher security. |
| Types | HTTP Proxy, SOCKS Proxy, Transparent Proxy, etc. | VPN protocols like OpenVPN, IKEv2, L2TP/IPsec. |
| Security | Limited to hiding the IP address, vulnerable to cyberattacks. | High security with encryption, protecting against hackers. |
| Cost | Often, free or inexpensive, premium options are available. | Typically, subscription-based, free VPNs may have limited features. |
| Best Use Cases | Bypassing geo-restrictions, managing bandwidth, and accessing restricted sites. | Online banking, secure browsing on public Wi-Fi, comprehensive privacy, and bypassing geo-blocking. |
How Does a Proxy Server Work?
Understanding how proxy servers work involves breaking down their roles and processes. Essentially, a proxy server acts as an intermediary between a client (such as a web browser) and a destination server (such as a web server).

- Initiating Client Request: When a user requests a resource (like a web page or file), the request is first sent to the proxy server, not directly to the destination server. This request usually includes the URL of the web resource.
- Processing the Request: The proxy server evaluates the request based on its rules and configurations. This can involve several actions:
- Filtering: Blocking access to certain websites based on predefined rules.
- Caching: Checking if the requested resource is already cached. If it is, the proxy can return the cached version, saving bandwidth and speeding up the process.
- Authentication: Requiring the user to authenticate before proceeding, adds an extra layer of security.
- Forwarding the Request: If the resource is not cached or if the request is configured to be forwarded, the proxy server forwards the request to the destination server on behalf of the client. During this process, the proxy uses its IP address to mask the client’s original IP address.
- Receiving the Response: The destination server processes the request and sends the response (such as a web page, file, or other data) back to the proxy server.
- Delivering the Response: The proxy server forwards the response from the destination server to the client. Once this step is completed, the user sees the requested resource in their browser.
How to Choose the Right Proxy Server?
Choosing the right proxy server requires understanding the needs and functions of different types of proxies, as well as potential risks.
Here are key factors to consider:
- Determine Your Purpose: Identify the primary reason for using a proxy server.
- Web Development and Testing: Simulate network conditions, access geo-restricted content for testing, and optimize request handling and response analysis during development.
- Improving Privacy and Anonymity: Protect identities and locations from online tracking.
- Security Enforcement: Build firewalls, block malicious traffic, and defend against cyber threats.
- Performance Optimization: Cache content, balance loads, and reduce latency to enhance performance.
- Understand the Types of Proxies: Proxy servers come in various types, each suited for different use cases.
- Forward Proxies: Regulate outgoing traffic from a network and increase privacy.
- Reverse Proxies: Manage incoming traffic, balance loads, and secure backend servers.
- Residential Proxies: Provide proper residential IP addresses for tasks like web scraping and accessing geo-restricted content.
- High Anonymity Proxies: Provide extreme privacy and anonymity.
- Assess Reliability and Speed: Proxy performance significantly impacts user experience; when evaluating proxies,
- Uptime Guarantees: Look for proxies that offer high uptime.
- Connection Speed: Ensure fast connection speeds to reduce latency and improve performance.
- Scalability: Choose a proxy that can handle increased traffic as your application grows.
- Evaluate Security Features: Security is crucial, especially when handling sensitive data.
- Encryption Support: Ensure the proxy offers encryption protocols like SSL/TLS to secure data transmissions.
- Authentication Mechanisms: Verify strong authentication methods to prevent unauthorized access.
- Malware Protection: Check if the proxy provides malware scanning or filtering to protect against threats.
- Scalability and Flexibility: As your needs grow, so may your proxy requirements.
- Scalable Solutions: Ensure the proxy can handle increasing traffic without significant performance degradation.
- Flexible Configurations: Look for options to adjust proxy settings as needed.
- Integration Capabilities: Ensure the proxy integrates well with your existing tools and platforms.
- Consider Cost and Budget: Proxy server costs vary based on features and performance.
- Free vs. Paid Proxies: While free proxies may seem cost-effective, they often have limitations such as slow speed, bandwidth restrictions, and security risks. Paid proxies generally offer better performance and security.
- Pricing Models: Some proxies charge based on bandwidth usage, while others offer flat-rate pricing for unlimited access.
- Value for Money: Compare the features and performance of a proxy against its cost to ensure it provides good value.
- Customer Support and Documentation: Reliable customer support and good documentation are essential for effectively managing proxy servers.
- Support Availability: Ensure the provider offers prompt and knowledgeable support for any issues.
- Resource Availability: Look for comprehensive documentation, tutorials, and FAQs to guide you through setup and management.
- Community and Forums: Access to active communities or forums can provide additional support and insights from other users.
Common purposes include:
This will help you select the appropriate proxy type and configuration for your needs.
Consider the following:
Choose the right type based on your specific use case.
Consider the following:
Consider the following:
Consider the following:
Consider the following:
Consider the following:
By carefully evaluating the factors outlined above, you can select a proxy server that meets your specific privacy, performance, and security needs. Modern testing platforms can be invaluable for advanced testing and seamless integration with proxy setups.
For example, if you’re involved in web development and testing, cloud-based platforms can enhance your proxy setup by enabling testing under various network conditions, including those facilitated by proxy servers.
Cloud testing solutions like LambdaTest is an AI-powered test execution platform that supports manual and automated testing across 3,000+ browser and OS combinations. Its robust integration capabilities allow you to simulate real-world scenarios while maintaining privacy and security.
It also provides secure access to network-restricted resources using a dedicated proxy server, ensuring comprehensive testing without compromising security or accessibility.
If your system is behind a proxy or firewall, you may have issues running tests on the LambdaTest Selenium Grid. To run tests behind a proxy, follow the support documentation: LambdaTest Proxy Setup.
Risks to Consider When Using Proxy Servers
While proxy servers offer many benefits, they also carry risks that users and organizations should be aware of. Understanding these risks is crucial for mitigating potential downsides and ensuring safe and effective proxy usage.
- Security Vulnerabilities
- Malicious Proxies: Some proxy servers are untrustworthy and may be set up by malicious actors to intercept login credentials or other sensitive data.
- Data Breaches: Poorly configured proxies can be vulnerable to attacks, leading to the exposure of sensitive information.
- Privacy Issues
- Logging: Some proxies maintain logs of user activities, which can be accessed by proxy server operators or third parties, raising privacy concerns.
- Unencrypted Data: Proxies without SSL (Secure Socket Layer) encryption expose data to interception and unauthorized access by attackers.
- Performance Issues
- Latency: Introducing a proxy server in the data path can increase latency, resulting in slower response times.
- Bandwidth Limitation: Some proxies impose bandwidth limitations, which can reduce Internet speeds.
- Reliability and Availability
- Downtime: Proxy servers can experience downtime or become overloaded, making them unavailable and disrupting Internet access.
- Dependency: Relying on a proxy server means that if it goes down, users lose access to the resources routed through it.
- Legal and Ethical Risks
- Illegal Use: Proxy servers can be used to bypass regional restrictions or engage in illegal activities, exposing users to legal liability.
- Blocked by Services: Many service providers actively scan and block proxy servers used to access streaming platforms and websites.
- Limited Functionality
- Compatibility Issues: Not all applications and services work well with proxy servers, leading to potential functionality issues.
- Geo-Location Misrepresentation: Proxies can sometimes provide inaccurate location data, affecting geo-specific testing results.
- Misconfiguration Risks
- Improper Configuration: Poorly configured proxies can expose internal networks and systems to security risks.
- Complexity: Setting up and maintaining a proxy server requires technical expertise. Mistakes can have significant security and performance consequences.
- Ethical Considerations
- User Consent: Using a proxy without user consent can be considered unethical, as it compromises privacy and trust.
- Content Manipulation: Some proxies may modify web page content, inject ads, or alter requests and responses, which can be misleading.
Conclusion
Proxy servers play an important role in modern web development and testing. They offer enhanced security, better performance, and improved accessibility. From simulating different network conditions to safeguarding sensitive data, they provide solutions to various challenges developers face. Selecting the right proxy server involves understanding your goals, evaluating proxy types, and ensuring scalability, security, and cost-effectiveness.
With solutions like LambdaTest dedicated proxy server, developers can streamline their workflows, securely access restricted resources, and deliver robust, high-quality applications. Making informed proxy server usage decisions optimizes the efficiency of your development processes toward attaining your project goals.
Frequently Asked Questions (FAQs)
Which device is used as the proxy server?
A proxy server is a dedicated computer or software system running on a computer that acts as an intermediary between an endpoint device, such as a computer, and another server from which a user or client is requesting a service.
How to create your own proxy?
- Click the Windows key from the keyboard and search proxy settings. Click to open it.
- Click on the Set up button under Manual proxy setup.
- In the next Window, Turn ON the proxy server toggle and Enter the Proxy IP address and Port number of the proxy account we just created.
How to use a proxy server in Chrome?
Initially, setting up a specific proxy in Chrome should not be difficult; just follow the following steps:
- Open Google Chrome.
- Go to Chrome Settings > Advanced > System > Open your computer’s proxy settings. ( or simply copy this link: chrome://settings/system)
- Edit your proxy settings.
- Click OK.
- Select Apply.
Citations
|
Got Questions? Drop them on LambdaTest Community. Visit now